- Date: July 15, 2025
Implementation of an Intelligent Cloud Firewall Log Analyzer with Real-Time Threat Detection Using Python
- Executive Summary
This project implements a Python-based real-time firewall log analyzer for cloud-hosted Linux virtual machines. It enhances the UFW firewall by detecting repeated suspicious activity such as port scans and dynamically blocking malicious IP addresses. The tool monitors UFW logs, logs incidents, generates daily reports for administrative review, and includes an optional email alert system. Testing was performed on an AWS EC2 Ubuntu instance using simulated attacks via nmap and log injection.
- Introduction
Firewalls are essential components in network security. Cloud-based virtual machines often face threats such as port scanning and brute-force login attempts. UFW (Uncomplicated Firewall) provides basic protection but lacks intelligent detection and automated responses. This project aims to enhance the UFW firewall by building a log analyzer that can detect and respond to real-time threats.
Objectives
- Monitor and parse firewall logs in real time.
- Detect repeated suspicious activity such as port scans.
- Automatically block attacker IPs using firewall commands.
- Generate log reports for administrative review.
Optionally send email alerts for suspicious activity.
Methodology / Implementation
a. Cloud VM Setup
- Deployed Ubuntu 204VM on AWS EC2.
- Enabled UFW firewall and logging.
- Log file: /var/log/ufw.log
Figure1: AWS EC2 instance dashboard
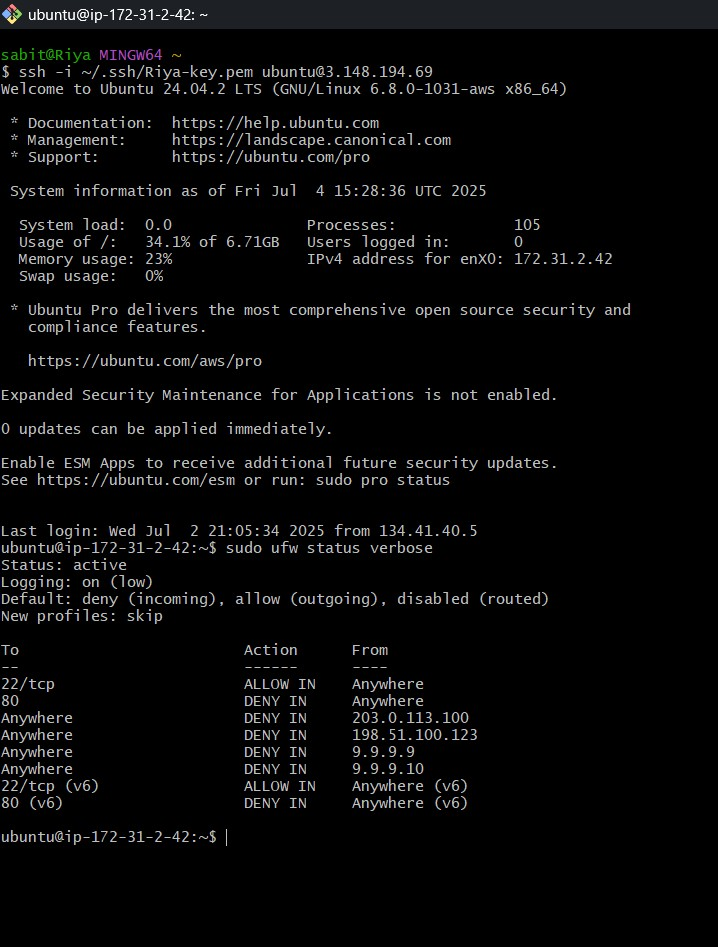
Figure 2: Terminal output of sudo ufw status verbose
b. Python Script Functionality
- Monitors log file using polling (tail -f style).
- Uses regex to extract IPs from lines containing [UFW BLOCK].
- Maintains a dictionary to count repeated IPs.
- Blocks IP using: sudo ufw deny from IP
- Logs the IP and timestamp in attack_log.txt and suspicious_ips.txt.
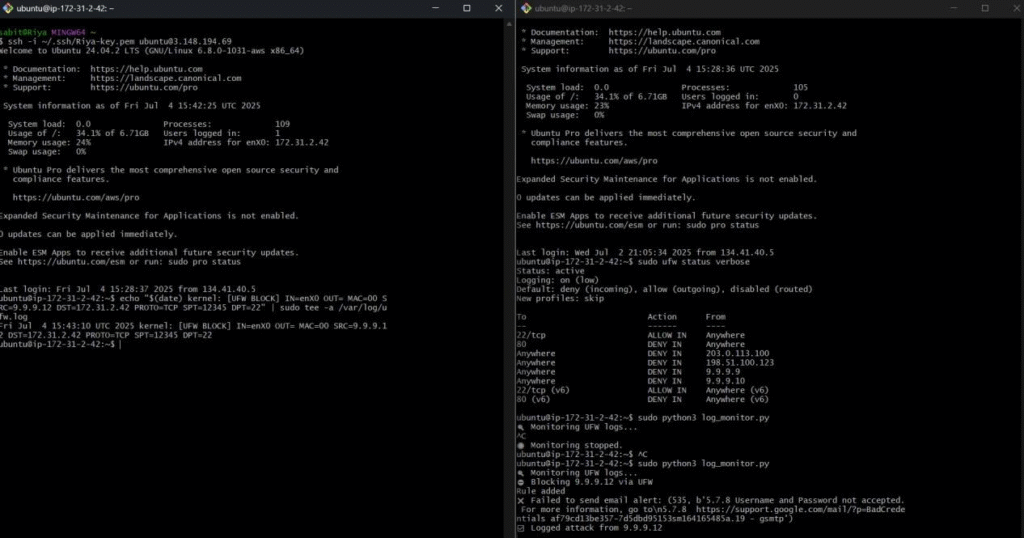
Figure 3: log_monitor.py code running
c. Testing the Script
- Used nmap from external host to simulate port scans.
- Injected manual log entries using echo and tee.
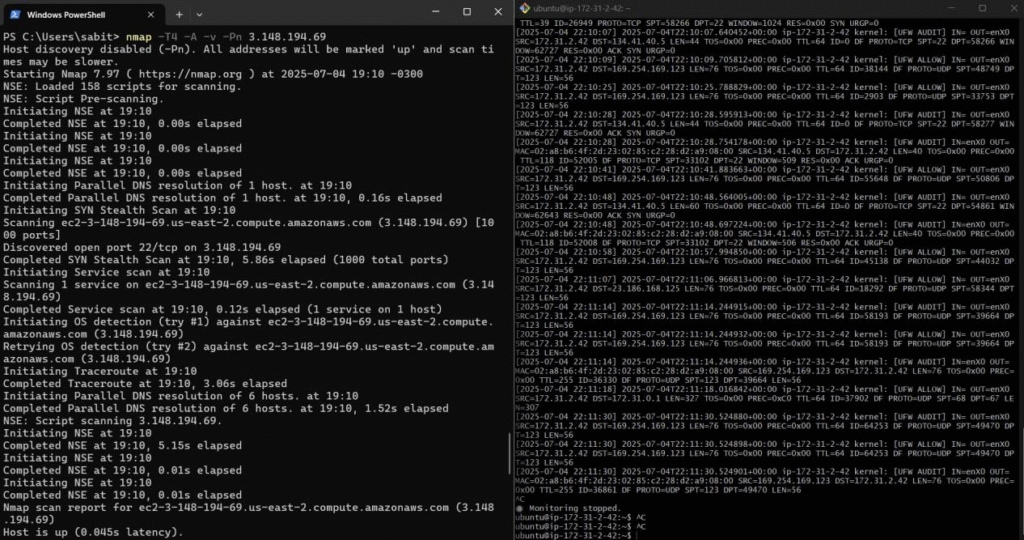
Figure 4: nmap scan from Windows command prompt
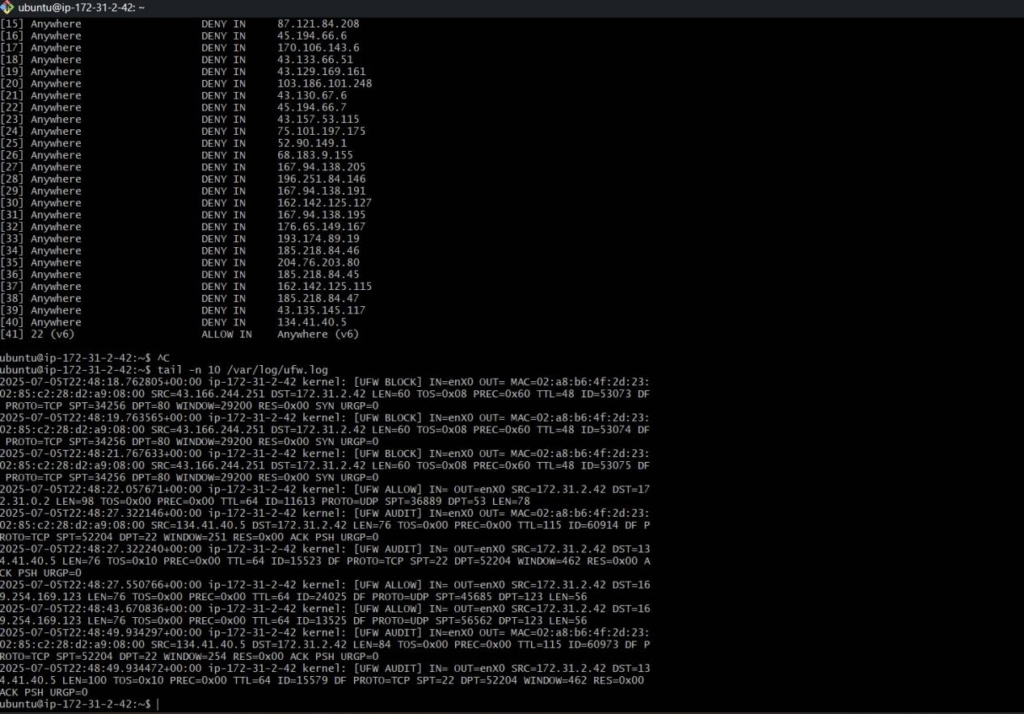
Figure 5: tail -n 10 /var/log/ufw.log
- attack_log.txt: Logs all blocked IPs with timestamps.
- suspicious_ips.txt: Stores permanently blocked IPs.
- generate_report.py: Creates daily summary in daily_report.txt
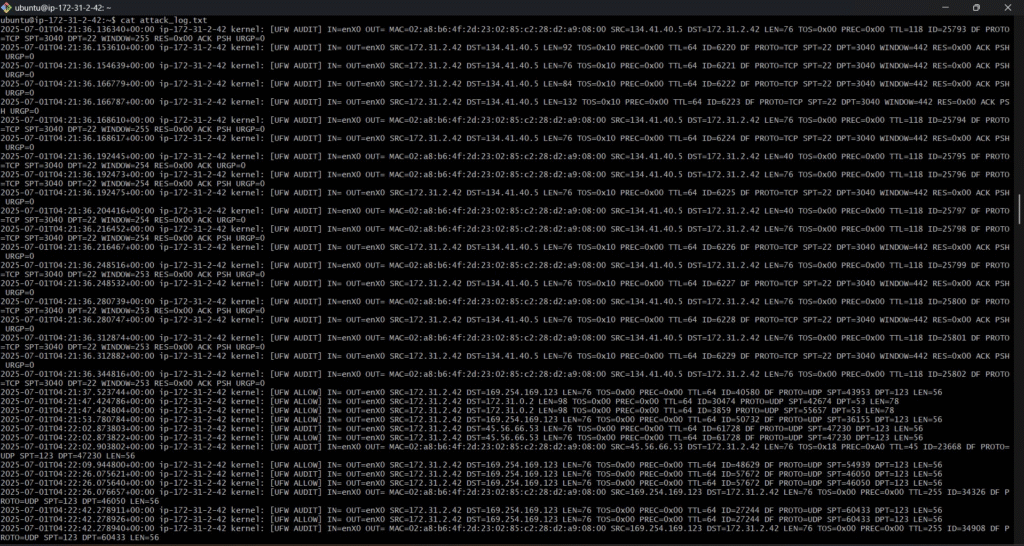
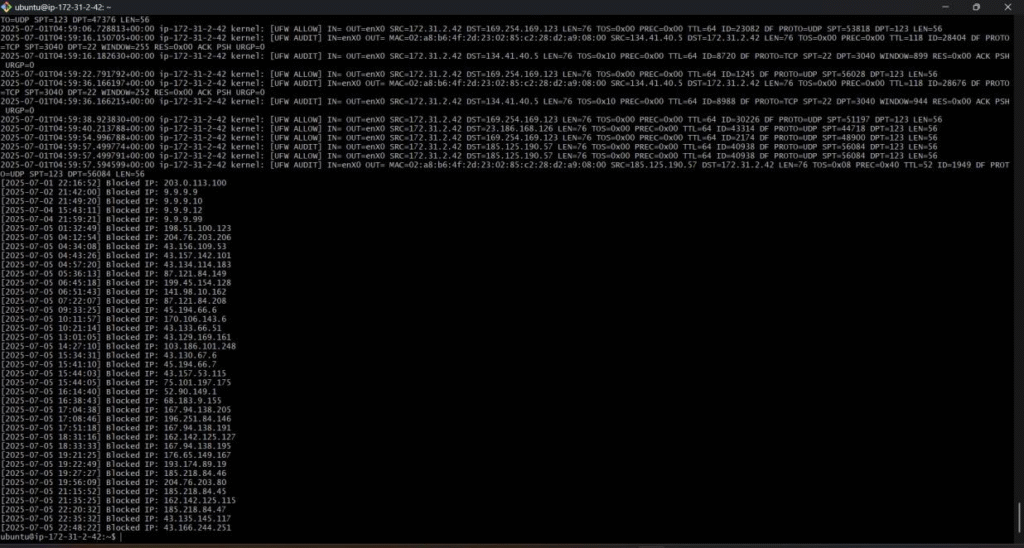
Figure 6: cat attack_log.txt
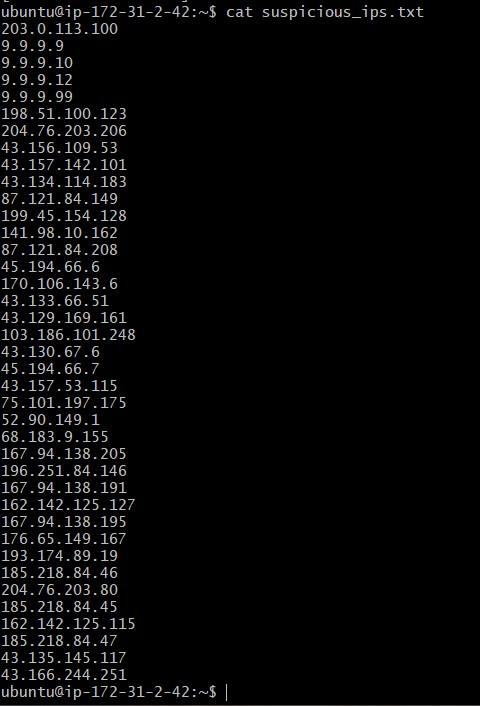
Figure 7: cat suspicious_ips.txt
Figure 8: Output from daily_report.txt
- Results
The script successfully detected repeated connection attempts, blocked malicious IPs via UFW, and recorded the events in log files. The daily report summarized all blocked events. The email alert feature was implemented but could not be tested due to SMTP login restrictions.
- Conclusion
This project implemented an intelligent real-time firewall log analyzer using Python, while enhancing the built-in UFW firewall on a cloud-hosted Ubuntu VM. The analyzer effectively blocked repeated attacks and maintained log files for review. Future improvements could include integration with webhook services (like Slack or Telegram) and dashboard visualization.
- References
https://manpages.ubuntu.com/manpages/focal/en/man8/ufw.8.html
https://docs.python.org/3/library/re.html
https://docs.aws.amazon.com/ec2/
https://support.google.com/mail/answer/7126229
https://owasp.org/www-project-logging/